Remember that static libraries are included in the size of the executable while
dynamic libraries are allocated at runtime so we will only see dynamic libraries
in the truss output.
The truss command becomes a valuable tool at this time. It is valuable because
we can then put a name to the different segments of the process. For
example, running "truss -o stat pops" gives us the following information:
execve("pops", 0x08047CA8, 0x08047CB0) argc = 1
open("/dev/zero", O_RDONLY, 01001076274) = 3
mmap(0x00000000, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE, 3, 0) = 0x8003C000
...
open("/usr/lib/libXm.so.1.2", O_RDONLY, 01001073564) = 5
read(5, "7F E L F010101\0\0\0\0\0".., 308) = 308
mmap(0x00000000, 1473456, PROT_READ, MAP_PRIVATE, 3, 0) = 0x8003E000
mmap(0x8003E000, 1347808, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED, 5, 0) =
0x8003E000
mmap(0x80188000, 117724, PROT_READ|PROT_WRITE|PROT_EXEC, MAP_PRIVATE|MAP_FIXED
,5, 1347584) = 0x80188000
mprotect(0x801A5000, 4096, PROT_READ|PROT_WRITE|PROT_EXEC) = 0
...
In kcrash, we can use the mmap addresses to determine which segments are
associated with each library. The mappings shown by kcrash should match those
of the truss output.
First, we run the 'ps' macro to obtain the address of the process we are
interested in. The name of the executable in this case is "pops":
S> ps
ADDRESS PID PPID UID FLAGS K U R WCHAN ST COMMAND
D1396400 06053 00001 00000 00102010 - - - D02F34CC SLEEP /usr/lib/saf/ttymon
D13EFE00 06052 06042 00103 00502010 - - - D02F34CC SLEEP ./pops
D13EEE00 06042 06041 00103 00102010 - - - D13EEE00 SLEEP -ksh
...
Then we run the 'procvm' macro to get the address of 'as' as explained in the
overview:
S> procvm D13EFE00
*p_seguslo D10EF968
*p_segu F0490000
*p_as D12D34E0
*p_trace 00000000
*p_exec D1253E98
p_pri 0000004E
p_usize 0002
u.u_psargs = "./pops "
Next we use the 'as' macro to obtain the address of the segment list:
S> as D12D34E0
as [D12D34E0]: keepcnt 000000 segs D14FCF80 seglast D13EFBE0 sz 30E000 rss 1CA
hat: pts D14F98C0 ptlast D14F9500 pdtp 00000000 cr3 D01C88B0 ref 0
Finally, as promised, we get to see all the segments of the process by using
the macro "seglst" and giving it the address in "segs" above.
S> seglst D14FCF80
ADDRESS DATA BASE NPGS MAP PROT VNODE OFFSET ANON_MAP SWPRESV
D14FCF80 D14FC920 08041000 0007 02 0F 00000000 FFFFB000 D1531000 00007000
D14FCF60 D14FC8FC 08048000 0055 02 0D D1253E98 00000000 00000000 00000000
D13EF900 D13EFD68 0807F000 0005 02 0F D1253E98 00036000 D13EB188 00005000
D1337920 D1337CFC 08084000 0048 02 0F 00000000 00000000 D1531150 00030000
D13EFBC0 D1322290 80000000 0056 02 0D D122B4E8 00000000 00000000 00000000
D13EFBA0 D132226C 80038000 0002 02 0F D122B4E8 00038000 D14FD3B8 00002000
D13EFB80 D1322248 8003A000 0001 02 0F 00000000 00000000 D15310A8 00001000
D152F040 D1322320 8003C000 0001 02 0B 00000000 00000000 D13DBAD8 00001000
D13EFBE0 D13222B4 8003E000 0330 02 0D D1241518 00000000 00000000 00000000
D152F0E0 D13223D4 80188000 0029 02 0F D1241518 00149000 D13DB8E0 0001D000
D152F020 D13222FC 801A5000 0001 02 0F 00000000 00000000 D15310E0 00001000
D152F100 D13EBE00 801A7000 0095 02 0D D124CCD8 00000000 00000000 00000000
D1337800 D14FC9B0 80206000 0003 02 0F D124CCD8 0005E000 D1531038 00003000
D152F140 D13EBE48 8020A000 0049 02 0D D1236CA8 00000000 00000000 00000000
D152F160 D13EBE6C 8023B000 0005 02 0F D1236CA8 00030000 D15311C0 00005000
D152F120 D13EBE24 80240000 0004 02 0F 00000000 00000000 D15311F8 00004000
D152F1A0 D13EBEB4 80245000 0062 02 0D D1240A28 00000000 00000000 00000000
D152F000 D13222D8 80283000 0004 02 0F D1240A28 0003D000 D1531188 00004000
D152F180 D13EBE90 80287000 0001 02 0F 00000000 00000000 00000000 00001000
D152F080 D1322368 80289000 0016 02 0D D123D148 00000000 00000000 00000000
D152F060 D1322344 80299000 0001 02 0F D123D148 0000F000 D1531118 00001000
D152F0C0 D13223B0 8029A000 0002 02 0F 00000000 00000000 00000000 00002000
D152F1C0 D13EBED8 8029D000 0004 02 0D D1221308 00000000 00000000 00000000
D152F0A0 D132238C 802A1000 0001 02 0F D1221308 00003000 D1531230 00001000
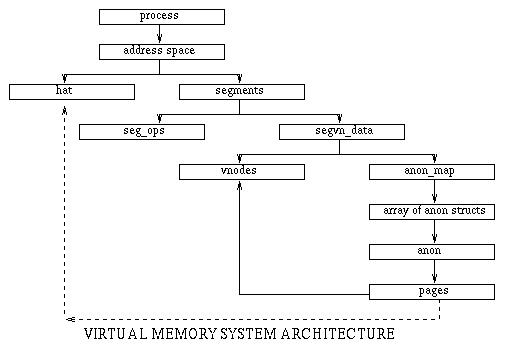
The address is the individual segment address. The data address is a pointer
to the segvn_data structure. The base address is the base virtual address of
the segment which matches the address given by truss. The 'npgs' gives the
number of pages used by the process. If NPGS is multiplied by 4096, it should
be equal to the value given by 'sz' from the address space macro. The MAP and
PROT are the file mappings and protections which we will discuss next. Then
the vnode of the segment is given, the offset, the pointer to the anon_map and
lastly the amount of swap that has been reserved for the segment.
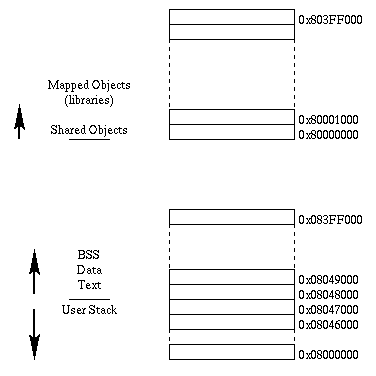
The first segment is the user stack. We can see this by the base address
08041000. The user stack is using 7 pages. A "MAP" value of 02 means
that the segment is MAP_PRIVATE and the 0F indicates that the segment has
user, executable, write and read (UEWR) permissions. There is also swap
associated with this segment.
See the mman.h include file for all the mappings and protections. The mapping
will either be shared or private.
The next segment should be the text segment of the executable. We should see
that this segment is shareable. The base address is 08048000 which is correct.
There are 55 pages, mapping is 02 or MAP_PRIVATE and the permissions are OD
or UE-R. No swap has been reserved. All of these add up to the fact that
this text segment is shareable. If there were swap associated with the
segment, it would not be shareable.
Following the text segment should be the data segment. We would not expect the
data segment to be sharable. We find that the segment starting at base
0807F000 is MAP_PRIVATE, UEWR permissions and has swap reserved. So, this must
be the data segment.
The last segment of the process should be the bss if it exists. Since we
have a segment starting at 08084000 it must be BSS. It has 48 pages, is
mapped MAP_PRIVATE, has UEWR permissions and has swap associated with it. It
is not shared.
The library starting at 80000000 which is not listed in the truss is the text
segment of libc.so.1. It is followed by its data and bss segments. At
8003C000 is the run time link editor (rtld) which has permissions of 0B or
U-WR. These four segments will always be mapped the same way.
Now, the next segment should be the text segment of libXm.so.1.2 which is the
first library listed in the truss output. Looking at the truss information,
we would expect it to have a beginning address of 0x8003E000. It does. Further
analysis shows us that the segment is shared as we would expect and the two
segments following appear to be the associated data and bss segments.
By again referring to the truss output, we would expect the next text segment
to begin at 0x801A7000 and so on.
The static executable has a total size of 30E000 or 782 pages (approx 3.2M).
Now let us compare it to the completely dynamically linked executable.